A Guide to Security Testing of API Endpoints
Testing your API endpoints for security isn't just a "nice-to-have" anymore; it's a critical step in finding and fixing vulnerabilities before someone else does. Think of it as actively trying to break into your own system to find the weak spots in authentication, authorization, and data handling. This proactive approach is what keeps sensitive information safe and your systems running smoothly.
Why API Security Testing Is Now Essential
APIs are the connective tissue of modern software. They're the couriers that ferry data between your mobile app, backend servers, and any third-party services you rely on. But because they're so central to everything, they've become a massive target for attackers.
Leaving an API unsecured is like leaving the main door to your data vault wide open. It's not a question of if it will be compromised, but when.
This guide is designed to be a practical roadmap, not just a theoretical discussion. We'll get into the nitty-gritty of how to uncover hidden vulnerabilities, set up automated security checks, and build a culture where security is baked in from the start. The goal is simple: protect your assets, keep your customers' trust, and avoid the kind of costly breach that can tank a company's reputation.
The Business Case for Proactive Testing
You just can't afford to ignore API security. A single breach can lead to devastating financial losses and destroy the trust you've built with your users. In today's interconnected world, a vulnerability in one API can cascade, putting entire partner ecosystems at risk.
As businesses rely more and more on APIs, the potential attack surface just keeps growing. This makes rigorous testing a fundamental business need. If you need a refresher on the basics, our guide on what is API testing is a great place to start.
"In a world built on APIs, security is not a feature—it's the foundation. Proactive testing is the only way to ensure that foundation doesn't crumble under pressure from sophisticated threats."
When you get security testing right, the benefits go far beyond just checking a compliance box. You end up building stronger, more reliable products that people can trust.
Key Benefits of a Strong API Security Strategy
A dedicated approach to API security testing delivers some serious advantages that directly impact your business's health and reputation.
- Prevent Data Breaches: This is the big one. Good testing is your best defense against unauthorized access to sensitive user and company data—exactly what attackers are after.
- Maintain Customer Trust: Security builds confidence. When you show you’re serious about protecting data, you earn customer loyalty, which is priceless in a crowded market.
- Ensure Business Continuity: An API outage or breach can bring your entire operation to a grinding halt, costing you real money every minute you're down. Solid testing keeps things running.
- Accelerate Development Cycles: Finding and fixing a security flaw early is exponentially cheaper and faster than dealing with it after launch. By "shifting left" and integrating security into the development process, you prevent security from becoming a last-minute bottleneck.
Decoding the Modern API Threat Landscape

Before you can even think about testing an API for security flaws, you have to know what you’re looking for. The modern threat landscape isn’t about broad, generic attacks; it’s about exploiting subtle, specific vulnerabilities that attackers have gotten very good at finding. Your job is to beat them to it.
The best place to start is the OWASP API Security Top 10. This isn't some academic paper—it's a practical, real-world list of the most common and damaging API security risks found in production systems. Think of it as your field guide to the enemy's playbook.
And make no mistake, this is an urgent problem. A staggering 99% of organizations recently admitted to having at least one API security incident. The biggest culprits? Injection flaws and Broken Object Level Authorization (BOLA), which were behind more than a third of all attacks. If you want to dig into the details, you can find more in the current API threat report from CybelAngel.
What Are the Key API Vulnerabilities?
Let's break down some of the most critical threats you'll face. We'll skip the dense jargon and use some simple analogies to make these concepts stick.
One of the most insidious vulnerabilities is Broken Object Level Authorization (BOLA). Picture an apartment building where every tenant's key is supposed to open only their own door. BOLA is like a system glitch where any key can mysteriously unlock every single apartment.
In API terms, this happens when an endpoint doesn't check if the user has permission to access the specific object they're asking for. An attacker might simply change a user ID in the URL—say, from /api/v1/orders/123 to /api/v1/orders/456—and suddenly they're looking at someone else's private order history.
Next up is Broken Authentication. This is when the very process of verifying a user's identity is flawed. It could be anything from weak password requirements and poorly managed access tokens to leaving a login endpoint wide open to brute-force attacks. It’s the digital equivalent of a security guard waving someone through a checkpoint without actually checking their ID.
Any solid API security testing strategy has to put BOLA and authentication flaws front and center. These two vulnerabilities account for a huge percentage of successful breaches, making them the low-hanging fruit for attackers.
More Threats to Keep on Your Radar
Beyond those two heavy hitters, there are several other risks that demand your attention. For instance, Injection flaws are an old-school attack that are still incredibly effective. This is where an attacker sends malicious data to an API, tricking the backend into executing it. It's like a vending machine that's been tricked into accepting a counterfeit bill—the attacker fools the system into doing something it was never supposed to do.
Here are a few other critical vulnerabilities from the OWASP list that your testing absolutely must cover:
- Excessive Data Exposure: This happens when an API sends back more data than the client application actually needs. The front end might only display the user's name and profile picture, but if the raw API response also includes their home address and phone number, an attacker can easily grab it.
- Security Misconfiguration: This is a catch-all for a ton of common mistakes: using default passwords, leaving server settings too permissive, or showing overly detailed error messages that reveal clues about your internal architecture.
- Improper Assets Management: This is what happens when you lose track of your own APIs. Old versions, forgotten "shadow" APIs, and undocumented endpoints are often left running without any security updates, creating a perfect, unguarded back door for attackers.
Common API Vulnerabilities and Their Business Impact
Understanding these vulnerabilities is one thing, but connecting them to real-world consequences is what gets everyone on board with security. An exploit isn't just a technical problem; it's a direct threat to the business.
The table below breaks down the top OWASP API security risks, explaining each threat in simple terms and outlining the potential damage an exploit could cause.
| Vulnerability (OWASP API Security Top 10) | Simple Explanation | Potential Business Impact |
|---|---|---|
| BOLA (Broken Object Level Authorization) | The API doesn't check if the user is authorized to access the specific data they requested (e.g., another user's account). | Data breaches, unauthorized access to sensitive customer information, regulatory fines (GDPR, CCPA), and loss of user trust. |
| Broken Authentication | Authentication mechanisms are weak or implemented incorrectly, allowing attackers to impersonate legitimate users. | Account takeovers, fraudulent transactions, reputational damage, and widespread data exposure. |
| Excessive Data Exposure | The API returns more data than the client needs, exposing sensitive information that should have remained private. | Leakage of PII (Personally Identifiable Information), intellectual property theft, and providing attackers with reconnaissance data. |
| Security Misconfiguration | The system is set up insecurely, often due to default settings, verbose error messages, or missing security headers. | System compromise, data breaches, and creating an easy entry point for more sophisticated attacks. |
| Injection Flaws | Attackers send malicious data (like SQL or command injections) that the API mistakenly executes as a command. | Complete database compromise, remote code execution on the server, denial of service, and full system takeover. |
As you can see, the ripple effects of a single API vulnerability can be devastating. This is why proactive and continuous testing isn't just a best practice—it's a core business necessity.
Choosing Your API Security Testing Method
Now that we've mapped out the common threats APIs face, the big question is: how do you actually find these vulnerabilities? Application security gives us a few powerful ways to do this, and each has its own sweet spot. Choosing the right method—or, more realistically, the right combination—is the foundation of a solid defense.
Think of it like building a house. You wouldn't just do one type of inspection. You’d have someone check the foundation, someone else inspect the electrical wiring, and another look at the plumbing. Each check happens at a different stage for a different reason. The same idea applies to how we approach the security testing of API endpoints.
Let's break down the three core methodologies: Static, Dynamic, and Interactive Application Security Testing. Getting a handle on how they work will help you build a smarter, more effective testing strategy.
Static Application Security Testing (SAST): The Blueprint Review
First up is Static Application Security Testing (SAST). This is your first line of defense. A SAST tool scans your application's source code, bytecode, or binary without ever actually running the program. It’s what we call a "white-box" approach because it sees everything on the inside.
Imagine an architect poring over the blueprints for a new building before anyone even breaks ground. They can spot design flaws, structural weaknesses, or code violations right there on paper. That's exactly what SAST does for your code. It looks for known vulnerability patterns, like the kind that lead to SQL injection or other dodgy coding practices, long before the application is even built.
The huge win here is catching things early. SAST can be plugged right into a developer’s workflow, giving them feedback almost instantly after they commit code. This nips security issues in the bud when they are cheapest and easiest to fix.
Dynamic Application Security Testing (DAST): The Real-World Break-In Test
While SAST is busy with the blueprints, Dynamic Application Security Testing (DAST) is testing the finished building. DAST works from the outside-in, poking and prodding a running application just like a real attacker would. It throws all sorts of malicious-looking requests at your API endpoints to see what sticks.
This is a "black-box" approach—the tester doesn't know anything about the code inside. It’s like hiring a professional to try and break into your new house. They aren't going to study the floor plans; they're going to jiggle doorknobs, test window latches, and see if they can bypass the alarm system to find real, exploitable weak points.
DAST is fantastic at uncovering runtime problems that you'd never find by just looking at the code. Things like server misconfigurations or broken authentication flows only show up when the application is live. For a closer look at how this works in practice, check out our guide on how to test REST APIs.
The infographic below really brings home how common OWASP API vulnerabilities can create massive security risks.
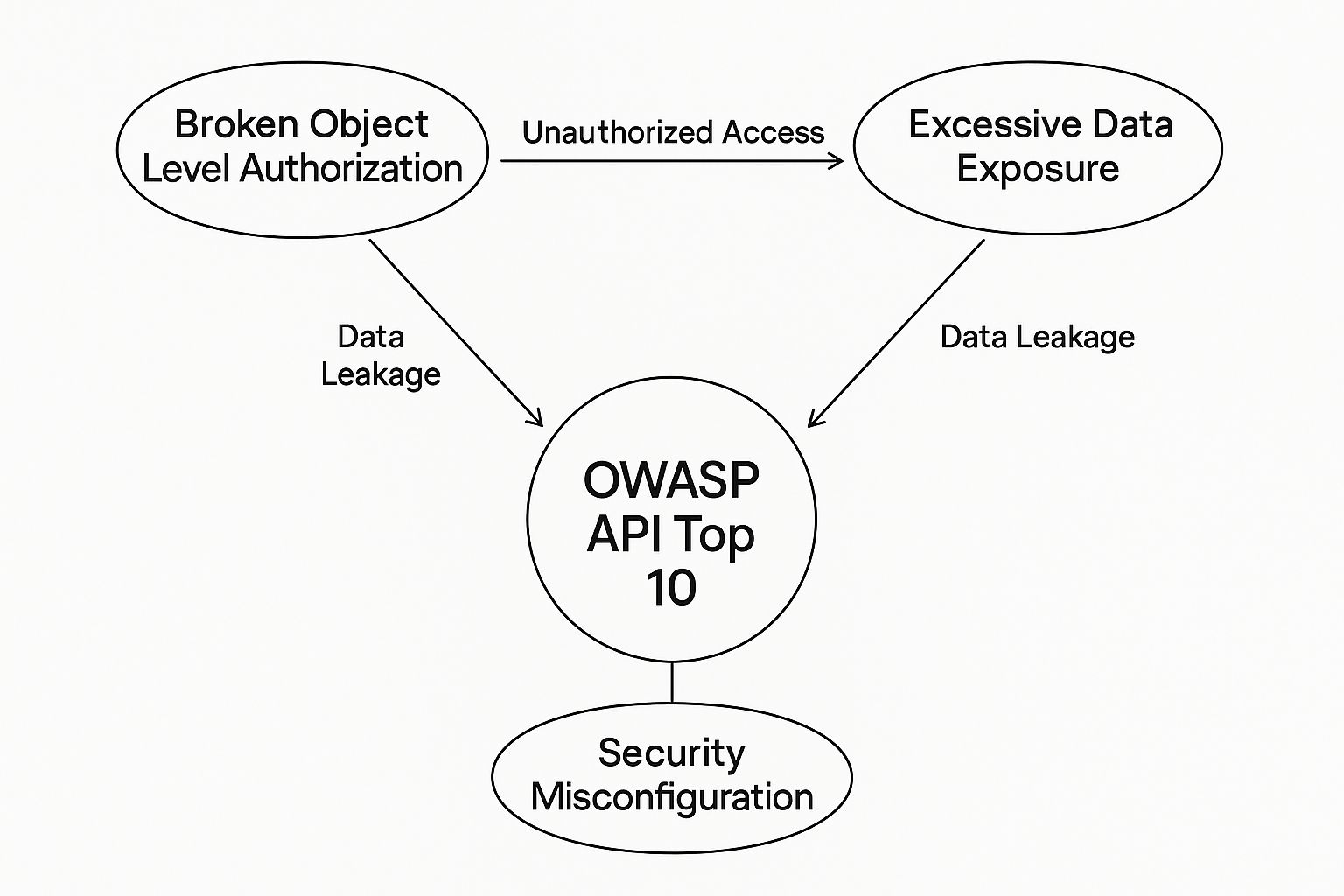
As you can see, a vulnerability like Broken Object Level Authorization isn't just a technical goof; it's a direct route for an attacker to access data they should never be able to see.
Interactive Application Security Testing (IAST): The Smart Internal Security System
Finally, we have Interactive Application Security Testing (IAST), which is a clever hybrid of the other two. IAST tools use special agents or sensors that you place inside the application while it's running. This gives them a unique vantage point—they can see both the application's code and its real-time behavior.
Think of IAST as a state-of-the-art security system installed throughout your house. It's always on, monitoring activity as people go about their day. If someone tries to use a key in the wrong lock, the system doesn't just sound an alarm—it instantly reports who did it, where, and when, providing all the context you need.
This inside-out view makes IAST incredibly accurate, which means way fewer false alarms for your team to chase down. Because it's running from within, an IAST tool can pinpoint the exact line of code that caused a vulnerability found during a test. That context makes it so much faster for developers to find the problem and fix it for good.
Each of these methods—SAST, DAST, and IAST—has a critical role to play in a complete API security testing strategy. SAST catches flaws at the source, DAST validates your defenses in a production-like environment, and IAST delivers deep, actionable insights. The most mature security programs don't pick one; they use a thoughtful mix of all three to make sure all their bases are covered.
How to Conduct a Hands-On API Penetration Test

Alright, let's move past the automated scanners. A real, hands-on penetration test is where you get inside an attacker's head. This is a methodical, creative process of poking and prodding for weaknesses that automated tools almost always miss—especially flaws buried deep in the business logic. We're not just running a script here; we're trying to find clever ways to chain different techniques together to uncover those critical security gaps.
A solid API pen test really comes down to a structured, three-phase game plan. By breaking it into reconnaissance, exploitation, and reporting, you create a thorough, repeatable process that gives your development team findings they can actually use.
Let's walk through what each phase looks like in practice.
Phase 1: Reconnaissance and Mapping
Every good attack starts with good intel. For API security testing, that means methodically mapping out your entire attack surface. The goal is simple: understand exactly what the API does, how it’s put together, and where the soft spots might be. You can't defend what you don't even know is there.
Your first move should be to grab any API documentation you can find, like OpenAPI or Swagger files. These specs are a goldmine, detailing every endpoint, the parameters they expect, and how they handle authentication. A tool like Postman is perfect for this, letting you import those specs and organize your requests from the get-go.
Once you’ve got the official endpoints down, it’s time to go hunting for the unofficial ones. Fire up the web or mobile app that consumes the API and watch the network traffic. This is where a proxy tool like Burp Suite or OWASP ZAP becomes your best friend, sitting between the client and the server and capturing every single request.
By watching the traffic, you can often spot "shadow" or "zombie" APIs. These are old, forgotten endpoints that are still live but aren't being maintained or secured. For an attacker, these are often the path of least resistance.
By the end of this phase, you should have a complete map of the API's territory. Make sure to document:
- All Endpoints: Every single endpoint you found, both documented and hidden.
- HTTP Methods: Which methods are allowed for each endpoint (GET, POST, PUT, DELETE, etc.).
- Parameters: A full list of query parameters, request body fields, and headers.
- Authentication: How does the API manage access? Note any API keys, JWTs, or OAuth tokens you see.
Phase 2: Active Exploitation
With a detailed map in hand, it's time to go on the offensive. This is where you actively try to break things. Your mission is to test for the vulnerabilities we've been talking about, focusing heavily on the OWASP API Security Top 10. You'll start crafting malicious requests designed to trigger these specific flaws.
For example, to test for Broken Object Level Authorization (BOLA), you might start by capturing a legitimate request to view your own profile (/api/users/123). Using a tool like Burp Suite's Repeater, you’d then just change the ID to someone else’s (/api/users/456) and resend it. If you get back their data, you’ve found a classic—and critical—BOLA vulnerability.
You'd then apply the same mindset to other common issues:
- Injection: Try feeding SQL commands or other malicious payloads into input fields to see if the backend blindly executes them.
- Broken Authentication: Can you bypass the login? Replay an old session token? Are password policies too weak?
- Excessive Data Exposure: Scrutinize the API's responses. Is it sending back sensitive info that the front-end client doesn't even use?
This hands-on work is absolutely critical. A recent study found that 85% of organizations in major Asia-Pacific economies had at least one API security incident last year, costing an average of over US$580,000 each. These aren't abstract risks; they have a real financial sting. You can find more details in the Akamai 2025 API Security Impact Study.
Phase 3: Reporting and Remediation
Finding a vulnerability is only half the job. The final, and arguably most important, phase is creating a clear, actionable report that helps developers actually fix the problems. A great pen test report isn't a "gotcha" list; it's a blueprint for improvement.
Structure your report for different readers. Start with a high-level executive summary that explains the risks in business terms. Then, dive into a detailed technical breakdown for the engineering team.
For every single vulnerability you find, you must include:
- A Clear Description: Explain what the vulnerability is in plain language.
- Steps to Reproduce: Give them the exact requests and steps needed to see the flaw for themselves.
- Proof of Concept: Show, don't just tell. Include screenshots or code snippets that demonstrate the exploit.
- Impact Assessment: Describe what could happen to the business if this flaw was exploited.
- Remediation Guidance: Offer specific, practical advice on how to patch the hole.
When you provide this level of detail, your findings become a concrete to-do list instead of an abstract problem. This collaborative approach makes API security testing a genuinely constructive process that makes everyone's work, and the entire application, stronger.
Integrating Security into Your CI/CD Pipeline

Real security isn't something you bolt on at the end. It needs to be part of the process from the very beginning. Waiting until your API is ready for release to start looking for vulnerabilities is a recipe for delays, budget overruns, and a whole lot of stress.
This is where the idea of "shifting left" comes in. The goal is to weave automated security testing directly into your Continuous Integration and Continuous Deployment (CI/CD) pipeline.
Think of it like a modern car factory. Quality checks aren't just done on the finished vehicle rolling off the line. They happen at every single station. If a bolt is loose or a wire is crossed, the line stops right there, and the problem gets fixed immediately. That's the same principle we want to apply to our code.
By baking security tools into your pipeline, you create an instant feedback loop that catches issues the moment they're introduced, not weeks later.
Automating SAST and DAST Scans
At the heart of a secure CI/CD pipeline are two key players we've already met: Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST). In an automated workflow, they each have a specific job.
SAST tools act like your code's building inspector. You configure them to automatically scan the source code every time a developer commits a change. This gives instant feedback on things like dodgy coding patterns or vulnerable third-party libraries before the application is even compiled.
DAST tools, on the other hand, are the crash test dummies. They get to work after the application is built and deployed to a staging environment. The pipeline triggers these tools to throw everything they've got at the live API endpoints, actively searching for runtime flaws like broken authentication or injection vulnerabilities.
This one-two punch ensures you’re checking for flaws in both the blueprint and the finished product. The aim here is to make the security testing of api endpoints as normal and routine as running unit tests.
Establishing Security Quality Gates
Putting the tools in place is step one. Making them stick is step two. That's what a security quality gate is for. It’s an automated checkpoint in your pipeline that enforces your minimum security standards.
If a scan finds a vulnerability that crosses a certain risk threshold, the gate slams shut, and the build is stopped in its tracks.
For instance, you can set up rules to:
- Fail the build if a SAST scan turns up any high-severity vulnerabilities.
- Block deployment to staging if a DAST scan finds something critical, like a SQL injection risk.
These gates are your non-negotiable safety net. They make it impossible for code with known, serious flaws to ever see the light of day in production. Your security policy goes from being a document to an automated, unbreakable rule.
This level of automation isn't just about security; it’s about speed. Inconsistent security standards create friction. In fact, research shows that over 55% of organizations experience software rollout delays because of API security problems, often stemming from weak governance. The 2025 API Threat Report from CybelAngel has some great insights on this challenge.
Fostering a Collaborative Security Culture
Maybe the biggest win from integrating security into your CI/CD pipeline is the cultural shift it creates.
When developers get immediate, clear feedback right inside the tools they already use—like GitHub, GitLab, or Jenkins—security stops being this annoying, separate thing that slows them down. It just becomes another part of writing good, solid code.
This tight feedback loop helps developers learn on the fly and build more secure coding habits naturally. It also breaks down the walls between development and security teams, turning what can sometimes be an adversarial relationship into a true partnership.
While automation handles the heavy lifting, it's all built on a foundation of clear agreements about how an API should behave. To get a better handle on that, check out our guide on what is contract testing for some crucial context.
Common Questions About API Security Testing
https://www.youtube.com/embed/5ZjRmTrl_ek
Even with a solid plan, API security can feel like a moving target. It’s completely normal to have questions pop up as you get deeper into the different tools, strategies, and everyday challenges.
To help you out, I’ve pulled together some of the questions I hear most often from teams just like yours. My goal is to give you straightforward, practical answers that you can actually use.
What Makes API Security Testing Different from Web App Testing?
This is a big one. While they sound related, testing an API's security is a whole different ballgame than testing a traditional web application. The fundamental difference is what you're actually looking at. Web app testing usually focuses on the user interface—what a person sees and clicks on in their browser.
API testing, on the other hand, is completely "headless." We throw the UI out the window and talk directly to the application's logic. Instead of clicking buttons, we're handcrafting raw HTTP requests to see how the API responds to different data payloads, like JSON or XML.
This direct line to the backend means we're hunting for a unique class of vulnerabilities that are often invisible from the front end. Think about things like:
- Broken Object Level Authorization (BOLA): This is a classic. Can a user just change an ID in an API call—say, from
/users/123to/users/124—and suddenly see someone else's private data? A UI would never let you do that, but an API might. - Excessive Data Exposure: Sometimes an API sends a ton of sensitive information back to the browser, and the front-end code is responsible for hiding what the user shouldn't see. An attacker can easily intercept that raw API response and see everything.
- Broken Authentication: Here, we're not just testing a login form. We’re probing the nitty-gritty of API keys, JWT tokens, and OAuth flows to find any crack that might let us impersonate a user or gain more power than we should have.
Because we’re operating at this level, our toolkit looks different, too. We rely on specialized tools like Postman to build requests and Burp Suite to intercept and mess with traffic, which is a world away from typical UI automation.
How Often Should We Test Our APIs for Security?
The only right answer here is: constantly. Great API security isn’t a one-and-done audit you check off a list. It needs to be a continuous habit, baked right into the way you build software.
The most effective strategy I've seen is a hybrid approach—you need different types of testing happening at different rhythms.
API security testing should be a continuous process, not a final gate. Combining automated vigilance with periodic, expert-led deep dives provides the most comprehensive coverage and prevents security from becoming a bottleneck.
For your day-to-day defense, automated scans are your best friend. By integrating SAST and DAST tools directly into your CI/CD pipeline, you can get security feedback on every single commit. This catches common slip-ups early and lets developers fix them on the spot.
But automation isn't a silver bullet. For a much deeper look, you absolutely need comprehensive manual penetration tests. These should be done periodically—at least once a year for all your APIs, and even more often for your most critical ones or after a major redesign. This is where a human expert uncovers the tricky business logic flaws that automated scanners are blind to.
What Are the First Steps for a Small Team to Get Started?
You don't need a huge budget or a dedicated security department to make a real difference. Even a small team can seriously level up its API security by focusing on the fundamentals with accessible tools.
Here’s a practical, three-step plan to get rolling:
- Create an API Inventory: You can't protect what you don't know you have. The very first step is to get a handle on every API your organization uses. Use a spec like OpenAPI (formerly Swagger) to create a clear, machine-readable map of all your endpoints, what they expect, and how they authenticate.
- Run Initial Automated Scans: You don't have to break the bank. Fantastic open-source tools like OWASP ZAP or the community edition of Burp Suite provide powerful scanning capabilities for free. Point them at your staging environment to quickly find the low-hanging fruit and common misconfigurations.
- Manually Test for the "Big Three": Focus your human effort where it will have the biggest impact. Start by hunting specifically for the top three OWASP API vulnerabilities: Broken Object Level Authorization (BOLA), Broken Authentication, and Excessive Data Exposure. Getting good at spotting these three flaws alone will drastically improve your security.
These foundational steps give you a strong starting point and deliver real security wins without a massive investment.
How Can AI and Machine Learning Improve API Security Testing?
This is where things get really interesting. AI and machine learning are shifting API security from a reactive chore to a proactive defense. Traditional security tools are great at spotting known attacks because they rely on predefined rules and signatures. But they often get tripped up by new or cleverly disguised threats.
AI thrives where those rigid systems fail. By analyzing huge amounts of API traffic over time, a machine learning model can build an incredibly detailed baseline of what "normal" looks like for each of your APIs—down to the typical request frequency, data patterns, and user behavior.
Once that baseline is established, AI can spot tiny deviations that signal an attack is underway in real-time. These are the kinds of subtle attacks that would sail right past a traditional firewall:
- Credential Stuffing: An AI can notice the unusual pattern of many failed login attempts coming from a wide range of IP addresses.
- Slow Data Exfiltration: It can detect an attacker who is siphoning off data bit-by-bit over a long period to stay below volume-based alerts.
- Bot Activity: AI is brilliant at distinguishing the robotic, predictable behavior of a script from the more chaotic patterns of a real human.
Some projections show that API-related incidents will soon account for over 90% of all web-based cyberattacks. As highlighted in a recent API security trends report, this makes AI-powered detection a critical layer of modern defense.
Testing complex failure states and edge cases is crucial for building resilient APIs, but it's risky to do in production. With dotMock, you can create high-fidelity mock APIs in seconds to safely simulate timeouts, 500 errors, and network failures without impacting your real systems. Stop waiting and start building more robust applications today. Get started for free at https://dotmock.com.