Your Guide to Proxy Server API Integration
At its heart, a proxy server API is a gateway that sits between your application and the wider internet. Instead of your app making a direct request to a website or another service, it sends that request through an intermediary server first.
This simple redirection is incredibly powerful. The proxy forwards your request on your behalf, which means the destination server only sees the proxy's IP address, not yours. This process provides a layer of anonymity, boosts security, and can even help you get around pesky geographic restrictions.
The Role of a Proxy Server API
Think of a proxy like a mail-forwarding service. You tell the service where you want your mail to go, and they handle the rest. The original sender never knows your final address; they only interact with the forwarding service. A proxy server API automates this entire process, letting your software manage it through code.
This API-driven approach is a game-changer. It allows your application to programmatically route its traffic through a vast, global network of servers without any manual setup. If you're new to the world of APIs in general, getting a handle on the basics is a great first step. This guide is a fantastic starting point: Understanding APIs: A Beginner's Guide.
How Does It Work Mechanically?
The mechanics are surprisingly simple. Your application builds a standard HTTP request—maybe to grab a webpage or fetch some data—but instead of pointing it at the final destination, it sends it to the proxy API's endpoint.
Your API call will include your credentials and the actual URL you want to reach. The proxy service takes it from there, picks a server from its massive pool (often based on a location you specify), and sends your request from that server's IP address.
A proxy server API acts as a middle-layer, decoupling your application's identity from its web requests. It intercepts, modifies, and forwards traffic, turning a direct two-way conversation into a managed three-party interaction.
Why This Is Important for Developers
For developers, this abstraction layer is a lifesaver. It provides scale, anonymity, and access that would be a nightmare to build and manage on your own. Imagine trying to maintain a private network of thousands of IP addresses spread across different countries—it's a massive undertaking.
A good proxy API handles all that infrastructure heavy lifting for you. This frees you up to focus on what your application actually does, while still getting the benefits of a robust, global network for critical tasks.
Here are a few common scenarios where this comes in handy:
- Large-Scale Data Collection: You can gather public web data or market intelligence without getting your IP address blocked.
- Accessing Geo-Restricted Content: It's perfect for testing how your site appears in other countries or verifying international ad campaigns.
- Enhancing Application Security: By masking your server's true IP, you can significantly reduce the risk of direct attacks.
- Load Testing: Simulating user traffic from all over the world becomes trivial, helping you find performance bottlenecks.
Ultimately, a proxy server API gives you fine-grained control over how your applications talk to the internet, offering a flexible solution to a whole host of technical and business problems.
Understanding Key Proxy API Patterns
A proxy server API isn't a one-size-fits-all solution. Think of it less like a single tool and more like a Swiss Army knife, with different attachments—or architectural patterns—built for specific jobs. Each pattern manages traffic with a unique goal in mind, so picking the right one is key to building a secure, efficient, and scalable system.
Let's walk through the four most common "personalities" a proxy can have. Understanding how they work will help you see where they fit into your own projects.
H3: Forward Proxies: The Outbound Gatekeepers
When most people hear the word "proxy," this is usually what they picture. A forward proxy sits between a private network—like your office computers—and the wider internet. It acts as a single, controlled exit point for all outbound traffic.
Imagine a company mailroom. Instead of every employee sending letters directly, everything goes through the mailroom first. The staff there can check for policy violations, log where mail is headed, and make sure everything is sent from the official company address. That's a forward proxy in a nutshell.
This setup is perfect for:
- Controlling Internet Access: Businesses use forward proxies to block access to certain websites or enforce acceptable use policies across their network.
- Caching Content: If everyone is visiting the same news site, the proxy can cache it. This speeds up access for everyone and saves on bandwidth.
- Anonymizing Users: From the destination server's point of view, all requests come from the proxy’s IP address, effectively hiding the individual user's IP.
H3: Reverse Proxies: The Inbound Receptionists
Now, flip that idea around. A reverse proxy sits in front of your web servers, intercepting all incoming requests from the internet. To the outside world, the reverse proxy looks like the actual server. It's the public face of your entire backend infrastructure.
This pattern is a cornerstone of modern web architecture. It’s no surprise that the proxy server service market was valued at $2.51 billion and is expected to hit $5.42 billion by 2033. With over 30 million developers using proxy APIs for everything from web scraping to managing high-traffic sites, their importance is clear. You can dig into the numbers and trends in the full report on proxy server services.
A reverse proxy's main jobs include:
- Load Balancing: It spreads incoming requests across multiple backend servers, so no single machine gets overloaded.
- Security: By hiding the true IP addresses and layout of your backend, it shields them from direct attacks like DDoS.
- SSL Termination: It can handle all the heavy lifting of encrypting and decrypting SSL/TLS traffic, freeing up your web servers to focus on their core tasks.
H3: API Gateways: The Specialized Managers
An API Gateway is really just a souped-up reverse proxy, but one that's been purpose-built to handle the unique challenges of API traffic. While a regular reverse proxy deals with general web traffic, an API gateway is all about managing, securing, and orchestrating your microservices and public APIs.
Think of an API Gateway as a highly intelligent air traffic controller for your APIs. It doesn't just route planes (requests); it also handles security screening, ticketing, and communication with the ground crew (backend services).
It centralizes a ton of critical API functions, like:
- Authentication and Authorization: Making sure only the right users and applications can access specific endpoints.
- Rate Limiting and Throttling: Protecting your backend services from being hammered by too many requests at once.
- Request/Response Transformation: Tweaking requests or responses on the fly to make sure different services can talk to each other, even if they don't speak the exact same language.
H3: Transparent Proxies: The Invisible Interceptors
Last but not least, we have the transparent proxy. This one is sneaky. It intercepts network traffic at the network level, so the user's device doesn't need any special configuration. In fact, users are often completely unaware it's even there.
Internet Service Providers (ISPs) and large corporations love these. Because they operate invisibly, transparent proxies are great for enforcing rules universally without anyone needing to opt-in. Think content filtering on a public Wi-Fi network or caching popular content to improve network speeds for an entire region. They get the job done without anyone ever knowing they were involved.
H3: Comparing Proxy Server API Patterns
To make things even clearer, let's put these four patterns side-by-side. Seeing their functions and use cases together really helps highlight what makes each one unique.
| Pattern | Primary Function | Common Use Case | Direction of Traffic Flow |
|---|---|---|---|
| Forward Proxy | To manage and control traffic leaving a private network. | Corporate networks filtering employee internet access. | Internal Clients → Proxy → Internet |
| Reverse Proxy | To manage and protect traffic entering a server environment. | Load balancing traffic across multiple web servers. | Internet → Proxy → Internal Servers |
| API Gateway | To manage, secure, and orchestrate API-specific traffic. | Centralizing authentication for a microservices architecture. | Internet/Clients → Gateway → APIs |
| Transparent Proxy | To intercept traffic invisibly at the network level. | ISP content filtering or caching for all customers. | Client ↔ Proxy ↔ Internet (User is unaware) |
Each pattern serves a distinct purpose, from guarding the exit door (forward) to acting as the public-facing receptionist (reverse). Choosing the right one depends entirely on what problem you're trying to solve.
Practical Use Cases for Proxy APIs
Knowing the theory behind proxy patterns is one thing, but the real "aha!" moment comes when you see them solving actual problems. A proxy server API isn't just a piece of technical plumbing; it's a versatile tool that tackles real-world business challenges. Think of it as an intelligent middleman, enabling strategies that would be incredibly difficult—or even impossible—to implement otherwise.
Let's dive into some of the most common and impactful ways these APIs are used every day.
Large-Scale Web Scraping and Market Intelligence
One of the most popular jobs for a proxy server API is large-scale web scraping. Businesses thrive on public data for everything from competitive analysis and price monitoring to market research. The problem? Firing off thousands of requests from a single IP address is the fastest way to get your server blocked.
A proxy API gets around this by automatically rotating through a massive pool of different IP addresses for each request. This makes your scraping activity look like organic traffic coming from countless different users, letting you gather the data you need without interruption.
- E-commerce: Retailers scrape competitor sites to keep an eye on pricing and stock levels in real-time, which feeds their own dynamic pricing models.
- Market Research: Firms collect data from news outlets, forums, and social media to gauge public sentiment and spot the next big trend.
- Lead Generation: Sales teams pull contact information from public directories and business listings to build out their prospect lists.
This infographic gives a great visual overview of the core proxy patterns that make these use cases possible.
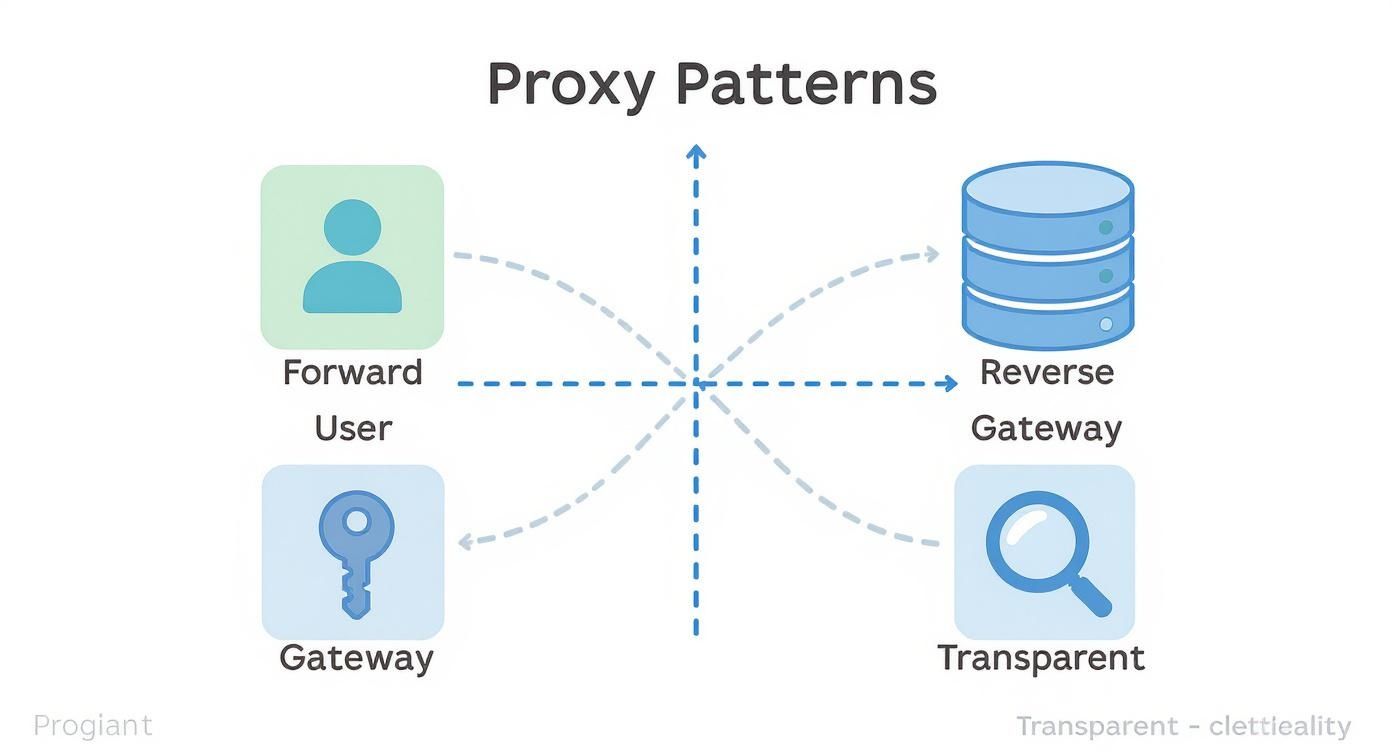
Each pattern has its specialty, from forward proxies managing user traffic to reverse proxies shielding servers, and each plays a distinct role in the digital ecosystem.
Geo-Targeted Content Verification and SEO Monitoring
How does your new ad campaign look to someone in Tokyo versus someone in London? Without a proxy, it's a guessing game. A proxy API with a global network of servers lets you route your traffic through specific cities or countries, so you can see exactly what your international users see.
This is a game-changer for a few key tasks:
- Ad Verification: Marketers can confirm their ads are showing up correctly in different regions and aren't appearing next to sketchy content.
- SEO Monitoring: SEO pros use proxies to check search engine rankings from various locations, since results can change dramatically based on the user's geography.
- Content Localization Testing: Development teams can make sure their site is properly displaying the right language, currency, and content for a global audience.
Advanced Security and System Management
Beyond just grabbing data, a proxy server API is a powerhouse for security and system management, especially when it's set up as an API Gateway.
By placing a proxy between your services and the open internet, you're essentially creating a bouncer. It inspects, filters, and controls every bit of traffic before it can knock on the door of your critical backend systems, giving you a powerful layer of defense and control.
Here are a few smart ways to put that control to use:
Implementing Rate Limiting
To fend off denial-of-service (DoS) attacks or just overly aggressive bots, you can configure your proxy to cap the number of requests a single client can make over a certain time. This is a simple but effective way to keep your backend from getting swamped.
Transforming API Requests
Ever had to connect a shiny new app to a dusty old legacy system? A proxy can play translator. It can intercept requests and change their format on the fly—say, from JSON to XML—to ensure the two systems can talk to each other without you having to rewrite either one.
Conducting Safe A/B Testing
A proxy can intelligently funnel a small percentage of live user traffic to a new version of a feature, while most users continue to see the old one. This lets you test new code in the real world with minimal risk. The new feature is safely isolated behind the proxy, allowing you to gather performance data from actual users before rolling it out to everyone.
How to Integrate Your First Proxy API
Let's move from theory to action. Understanding what a proxy server API is is one thing, but seeing it work is where the magic really happens. This guide will walk you through everything you need to know to get your first integration up and running, from choosing a service to making that first proxied request. We'll use some practical code examples to make it all crystal clear.
The demand for secure, automated access to web data has caused the global proxy server API market to explode. It was recently valued at $5.42 billion and shows no signs of slowing down. This growth is driven by things like web scraping and ad verification, with an incredible 78% of Fortune 500 companies now using proxy networks to power their operations.
Step 1: Choose Your Provider and Get Credentials
First things first, you need to pick a proxy API provider that aligns with what you're trying to do. Providers vary quite a bit in the types of proxies they offer (like residential, datacenter, or mobile), how they charge, and the size of their IP pool. Once you've signed up, you'll find your API credentials waiting for you in your user dashboard.
Typically, these credentials include:
- An Endpoint or Hostname: The address of the proxy server.
- A Port Number: The specific port you'll connect through.
- A Username: Your account identifier.
- A Password or API Key: The secret key that proves it's you.
Treat these details like any other password—keep them safe and secure.
Step 2: Constructing a Proxied API Request
Got your credentials? Great. Now you can build an API call that routes through the proxy. The whole idea is to tell your HTTP client to send its request to the proxy server instead of sending it directly to the target website. The proxy takes it from there and forwards it on your behalf.
A common convention for structuring this is username:password@hostname:port. It’s a clean and simple format.
A typical proxy URL structure
proxy_url = "http://YOUR_USERNAME:[email protected]:8080"
Let's look at how to pull this off in both Python and JavaScript.
Python Integration with the Requests Library
If you're a Python developer, the requests library makes this almost too easy. All you need to do is create a dictionary that defines the HTTP and HTTPS proxies and then pass it along with your request.
import requests
Your proxy credentials
proxy_user = 'YOUR_USERNAME'
proxy_pass = 'YOUR_PASSWORD'
proxy_host = 'proxy.example.com'
proxy_port = '8080'
The URL of the target website
target_url = 'https://api.example.com/data'
Structure the proxies for the requests library
proxies = {
'http': f'http://{proxy_user}:{proxy_pass}@{proxy_host}:{proxy_port}',
'https': f'https://{proxy_user}:{proxy_pass}@{proxy_host}:{proxy_port}',
}
try:
# Make the request through the proxy
response = requests.get(target_url, proxies=proxies)
# Check the response
print(f"Status Code: {response.status_code}")
print("Response Body:", response.json())
except requests.exceptions.RequestException as e:
print(f"An error occurred: {e}")
This little snippet tells requests to funnel the entire call through your designated proxy server, and it handles the authentication for you. If you're looking for a hands-on project to apply this, check out this guide on building a simple web scraper with Python.
JavaScript Integration with Axios
For the JavaScript crowd, especially those working in a Node.js environment, axios is the go-to library. It takes a little more setup, but the core concept is identical. You'll need to bring in an agent like https-proxy-agent to manage the connection.
const axios = require('axios');
const { HttpsProxyAgent } = require('https-proxy-agent');
// Your proxy credentials
const proxyHost = 'proxy.example.com';
const proxyPort = 8080;
const proxyUser = 'YOUR_USERNAME';
const proxyPass = 'YOUR_PASSWORD';
// The URL of the target website
const targetUrl = 'https://api.example.com/data';
// Create the proxy agent
const proxyUrl = http://${proxyUser}:${proxyPass}@${proxyHost}:${proxyPort};
const httpsAgent = new HttpsProxyAgent(proxyUrl);
// Configure axios to use the agent
axios.get(targetUrl, { httpsAgent })
.then(response => {
console.log(Status Code: ${response.status});
console.log('Response Body:', response.data);
})
.catch(error => {
console.error(An error occurred: ${error.message});
});
This setup instructs axios to tunnel its HTTPS requests through our proxy agent, which takes care of the connection and authentication with your proxy server API.
Integrating Proxies with Development Tools
Going beyond simple API calls, a proxy server API really shines when you weave it into your development workflow. Tools like dotMock let you intercept, inspect, and even create fake "mock" responses for your API traffic.
By enabling proxy mode in a tool like dotMock, you can route your application's traffic through it to record real API interactions or serve mock responses. This creates a highly realistic testing environment where you can simulate failures, latency, or specific data scenarios without touching a live server.

The screenshot above shows just how intuitive a modern tool can make this process. This kind of control is a game-changer for hunting down tricky API bugs and making sure your application is truly resilient. To see how to get started, you can find more details in our guide on https://dotmock.com/docs/features/proxy-mode.
Balancing Performance, Security, and Cost
When you bring a proxy server API into your stack, you're not just adding a tool—you're making a strategic trade-off. It’s a constant balancing act between three critical factors: speed, security, and cost. If you lean too far in one direction, the others will suffer. It's like tuning a race car; you can't just maximize horsepower without considering the brakes and the fuel efficiency.
Getting this balance right from the start is the key to building something that's not just functional, but also fast, safe, and sustainable. Let's break down how to navigate these competing priorities.
Performance and Network Latency
Here’s the unavoidable truth: routing traffic through a proxy adds an extra hop to its journey. That extra stop introduces network latency—the tiny delay between when you send a request and when you get a response. We're often talking milliseconds here, but those milliseconds can add up and make your application feel sluggish.
Think of it like sending a package from New York to Los Angeles. A direct flight is fastest. But if you route it through a sorting facility in Chicago, it’s going to take a bit longer. Your goal is to make that layover as short and efficient as possible.
Here's how you can keep latency in check:
- Pick Your Geography: Choose proxy servers that are physically close to your target API or website. Shorter distances mean faster travel times for your data.
- Invest in Quality Networks: Reputable proxy providers use premium, low-latency infrastructure. A bargain-bin service might save you a few bucks, but it'll likely route your traffic through slow, congested digital backroads.
- Optimize Your Connections: Use techniques like connection pooling and keep-alive headers. This lets you reuse existing connections instead of setting up a new one for every single request, which cuts down on overhead.
Security and Trust
The biggest security win with a proxy is IP masking. By hiding your server's real IP address, you shield it from direct attacks. But this protection comes with a new responsibility: you're now handing your data over to a third-party service.
A proxy server API becomes the middleman for your data. Choosing a shady provider is like hiring a security guard with a criminal record—you might be creating a bigger risk than the one you're trying to solve.
You absolutely have to do your homework. Dig into the provider's privacy policy, check their reputation in the community, and look for clear evidence of strong security practices. And please, stay away from "free" proxy services for anything important. They often make money by logging your activity or selling your data.
Cost and Pricing Models
Finally, you need to make the numbers work. The global proxy server market was valued at $3.4 billion and is expected to hit $7.2 billion by 2031, which shows just how many businesses are wrestling with these costs. With its history of early tech adoption and heavy cybersecurity investment, North America is a major player in this space. You can dive deeper into these global market trends and projections if you're curious.
Proxy providers generally structure their pricing in a few common ways:
- Pay-Per-Request/GB: You're billed for exactly what you use. This is perfect for projects with unpredictable traffic spikes or infrequent needs.
- Subscription Plans: You pay a flat monthly fee for a set amount of bandwidth or a certain number of requests. This gives you predictable costs for steady, consistent workloads.
- Per-IP Plans: You pay for exclusive access to a block of IP addresses. This is a must-have for use cases that require stable, unchanging IPs.
When you're calculating the cost, don't forget about external factors like rate limiting. If the API you're hitting has aggressive limits, you'll have to rotate through IPs more often, which can quickly increase your spending. We've put together a guide that explains how to manage API rate limits effectively in our detailed guide.
Best Practices for Managing Proxy APIs

Getting your proxy server API integrated is really just the beginning. The real work is making sure your application stays reliable, scalable, and secure over time. This means you need a smart operational strategy. By adopting a handful of best practices for both your production and development environments, you can guarantee better uptime and data quality.
Think of this as operational discipline. It helps you dodge common headaches like getting your IPs banned, dealing with corrupted data, or watching performance grind to a halt. When you get this right, your proxy setup becomes a powerful and dependable part of your tech stack. Let’s walk through the key practices that will give you the confidence to deploy.
Best Practices for Your Production Environment
When your application is live, reliability is everything. The mission is to build a system that can take a punch, handle failures gracefully, and keep running at peak performance.
Use Smart IP Rotation: Don't just shuffle your IPs at random. You need intelligent rotation logic that avoids hitting the same target with the same IP address too often. For any kind of high-volume work, a large, diverse IP pool is your best friend—and your strongest defense against getting blocked.
Build Solid Error Handling: Network requests are going to fail. It’s a fact of life. Your code needs to be ready for it. Implement automated retry logic, preferably with exponential backoff. If a request bombs, just wait a moment before trying again, and increase that delay with each subsequent failure. This simple trick keeps you from accidentally hammering a server that’s already struggling.
Keep an Eye on Performance: You have to monitor your key metrics. Track your success rates, response times, and error codes constantly. Set up alerts for any weird spikes in failures or latency. This lets you jump on issues and fix them before your users or data pipelines ever notice something is wrong.
Best Practices for Development and Testing
You can save yourself a world of pain by testing thoroughly before you even think about shipping to production. Your development environment should be your sandbox for breaking things and simulating real-world chaos.
Good testing isn't just about making sure things work. It's about intentionally breaking them. By simulating different geographic locations and messy network conditions, you're preparing your app for the wild, unpredictable internet. That's how you build something truly resilient.
This mindset ensures your application can handle the messy reality of a global user base.
Here are a few essential testing strategies:
Simulate Different Geographic Locations: Use your proxy server API to see how your app behaves when accessed from various countries. This is absolutely critical for checking things like content localization, ad targeting, and making sure you’re compliant with region-specific rules.
Test for All Kinds of Network Conditions: Never assume your users have a lightning-fast connection. You can configure your proxy or use a tool like dotMock to mimic slow networks, high latency, and spotty connections. This helps you build an experience that still works even when the network isn’t cooperating.
Lock Down Your Endpoints: Security isn't just a production problem. It starts in development. By implementing strong authentication and access controls early on, you prevent vulnerabilities from making it out the door. For a complete rundown, check out our guide on API security best practices for a checklist to keep your services safe.
Frequently Asked Questions
As you get deeper into proxy server APIs, a few questions tend to pop up again and again. Let's tackle some of the most common ones to clear the air.
What’s the Difference Between a Proxy API and a VPN?
It’s easy to mix these two up since both can hide your IP address, but they solve very different problems. Think of a VPN as a personal privacy shield. When you turn it on, it creates an encrypted tunnel for all the internet traffic coming from your device, whether that's your web browser, email client, or a game. It's all about user-level anonymity.
A proxy API, however, is a developer's tool. It operates on a request-by-request basis within an application. Instead of blanketing your entire device, it lets you programmatically route specific API calls or web requests through another server. This gives you fine-grained control for things like data scraping, load balancing, or getting around geo-restrictions—tasks a VPN just isn't built for.
Should I Build My Own Proxy Solution or Buy One?
The classic build vs. buy question. While you could technically spin up your own proxy server, it's a monumental effort. You'd be on the hook for acquiring a massive pool of global IP addresses, and then you’d have to manage, rotate, and maintain them constantly. It's a full-time infrastructure job that’s both incredibly complex and expensive.
For almost everyone, buying access from a commercial proxy provider makes way more sense. You get instant access to a reliable, professionally managed network that scales with your needs. This lets you concentrate on what your application actually does, rather than getting bogged down in the endless headache of IP management.
Choosing a provider essentially outsources the immense operational burden of IP management, ensuring higher success rates and letting you scale on demand without the risk of building and maintaining a fragile in-house system.
How Do I Pick the Right Type of Proxy?
The best proxy for the job really depends on what you're trying to accomplish. Each type has its own strengths, so matching the proxy to your goal is key.
Here’s a quick breakdown:
- Datacenter Proxies: These are your workhorses. They’re fast, cheap, and great for high-volume tasks where the target site doesn't have super-strong bot detection.
- Residential Proxies: When you need to look like a genuine user, these are what you want. The IPs come from real home internet connections, which makes them incredibly effective at getting past sophisticated security measures.
- Mobile Proxies: If your target is mobile-first or you're testing how an app behaves on a cellular network, these are the way to go. They use IPs from mobile carriers, which is essential for certain platforms.
Ready to build resilient applications with powerful, zero-configuration API mocking? dotMock lets you simulate any scenario, from network failures to specific error codes, so you can test, debug, and ship with confidence. Get started for free at dotmock.com.